
Setting up a hacking lab with Kali Linux and Metasploitable, Part 1 | The Best C# Programmer In The World - Benjamin Perkins

How to install Kali Linux with Win-KeX (GUI) in WSL2 (Windows Subsystem for Linux) - Ethical hacking and penetration testing

List of best Kali Linux tools for penetration testing and hacking - Linux Tutorials - Learn Linux Configuration
![How to Hack Exploit Windows Using Metasploit Beginners Guide - HackingPassion.com : root@HackingPassion.com-[~] How to Hack Exploit Windows Using Metasploit Beginners Guide - HackingPassion.com : root@HackingPassion.com-[~]](https://hackingpassion.com/how-to-hack-exploit-windows-using-metasploit-beginners-guide/featured-image.png)
![How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/5-74.png)
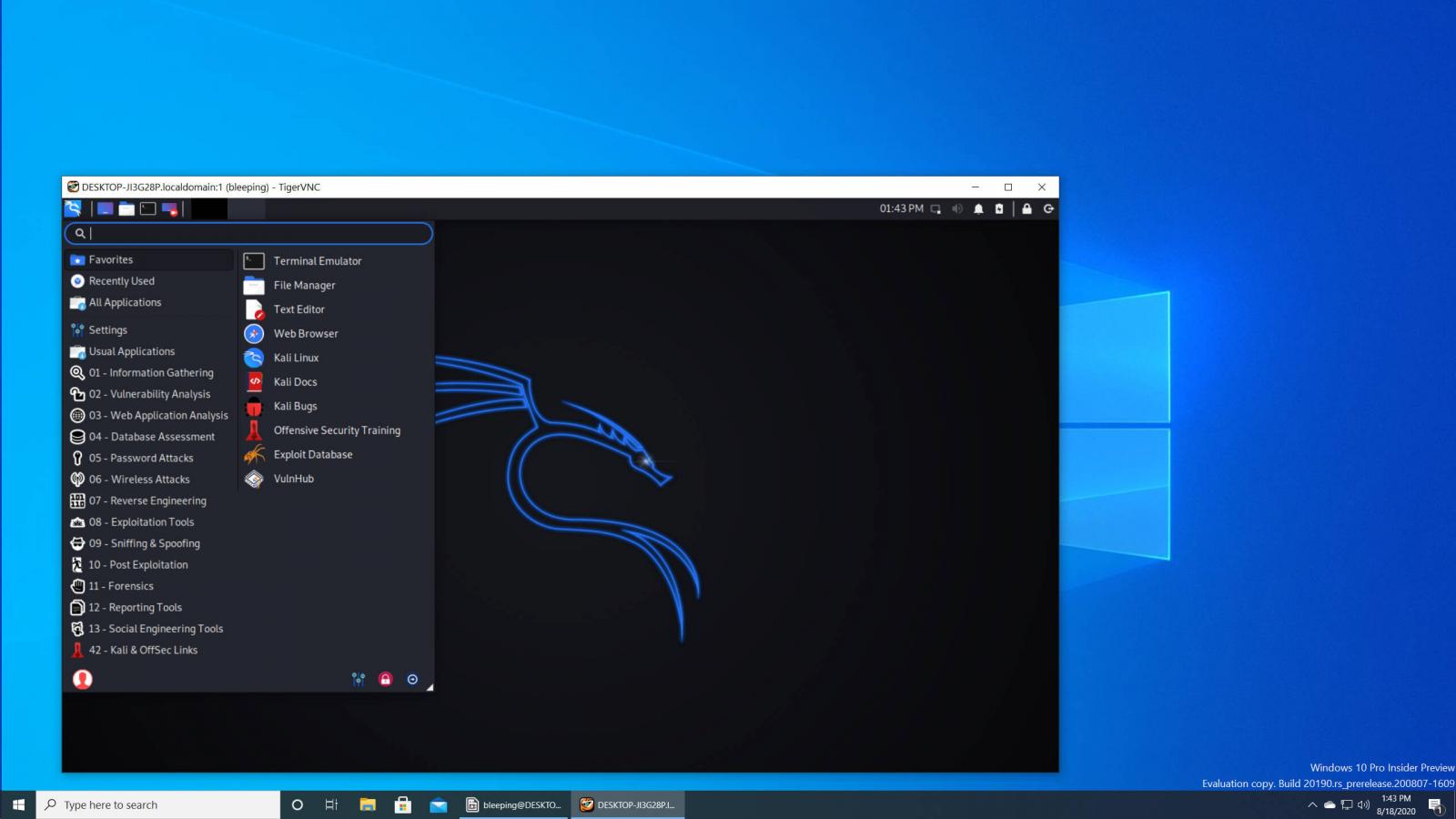
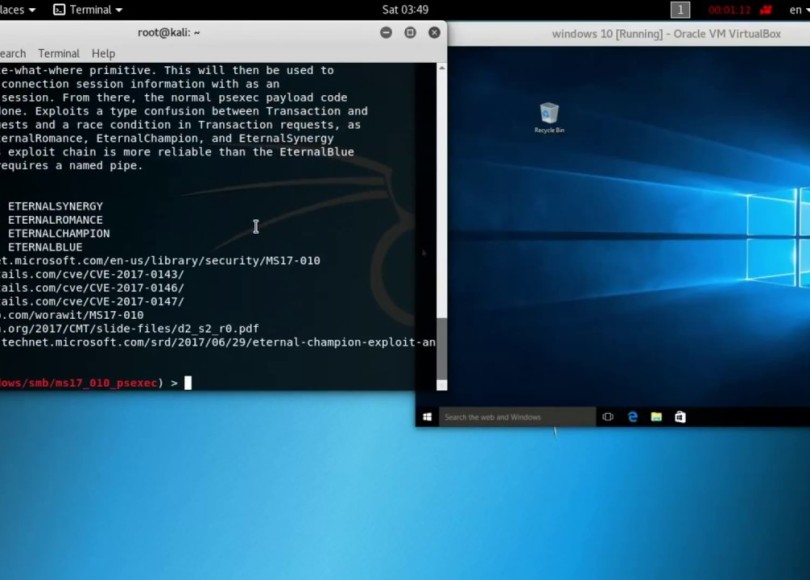
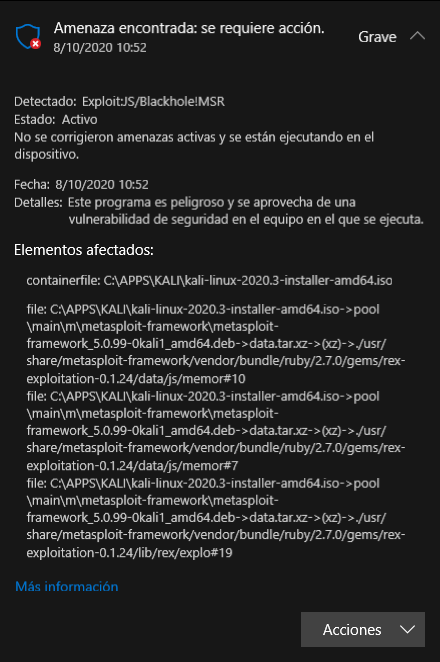

![How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/9-23.png)




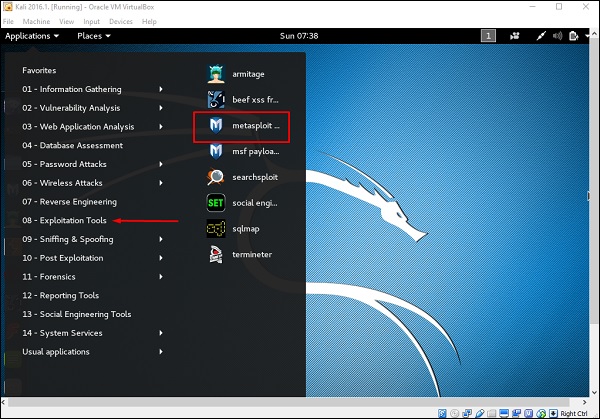
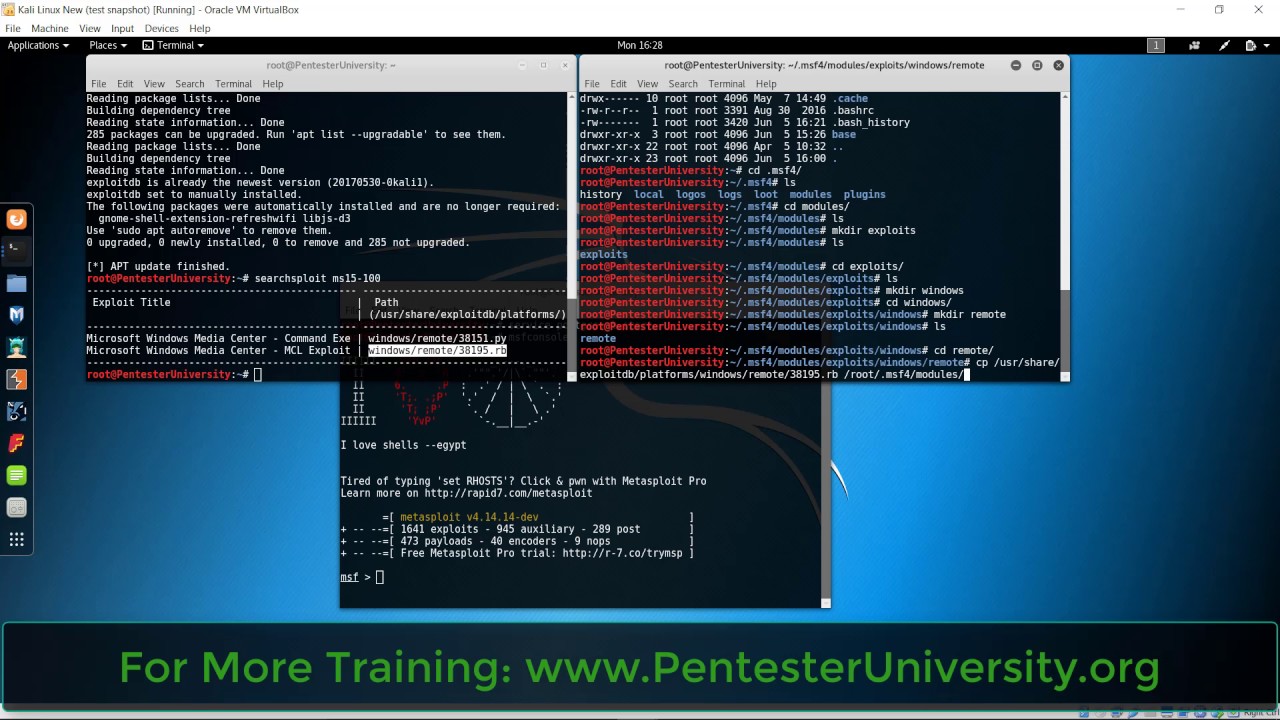


![How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/14-10.png)