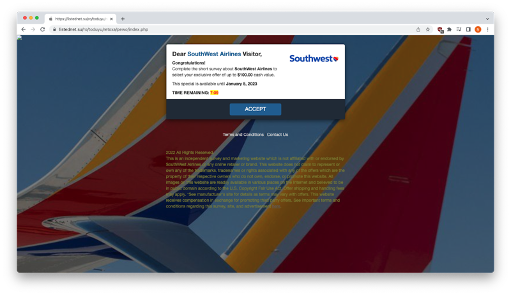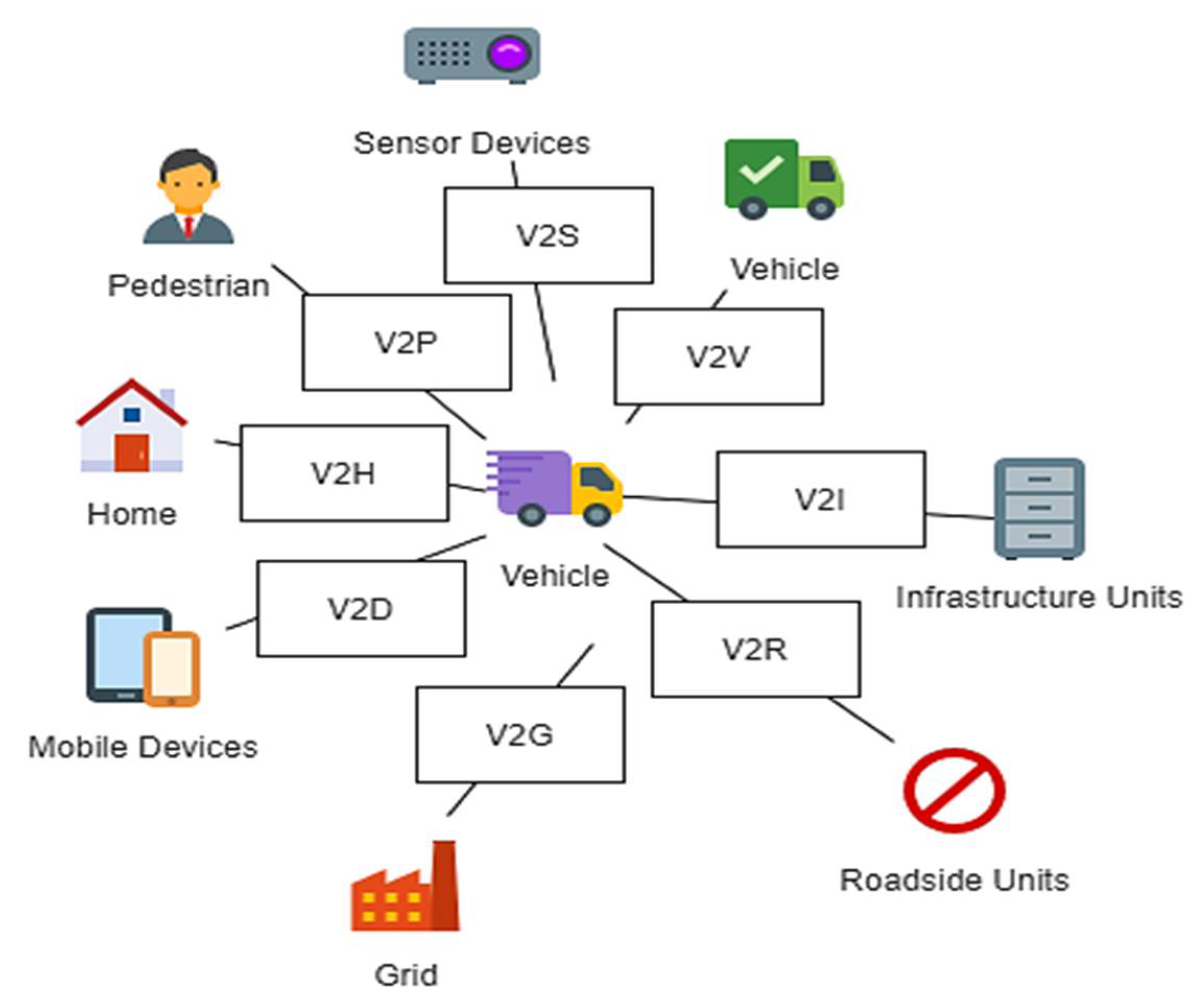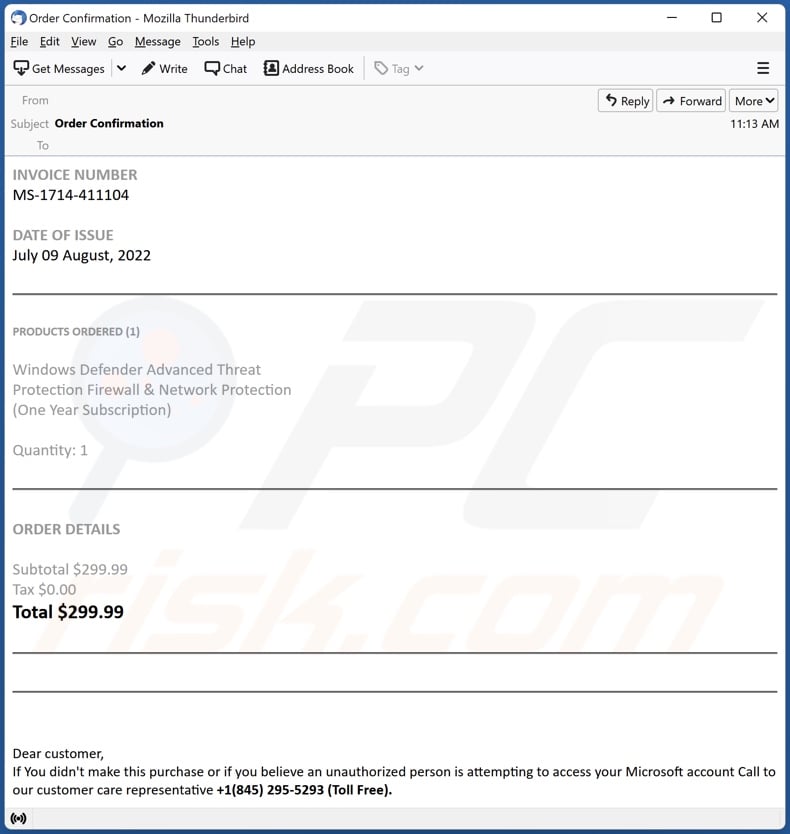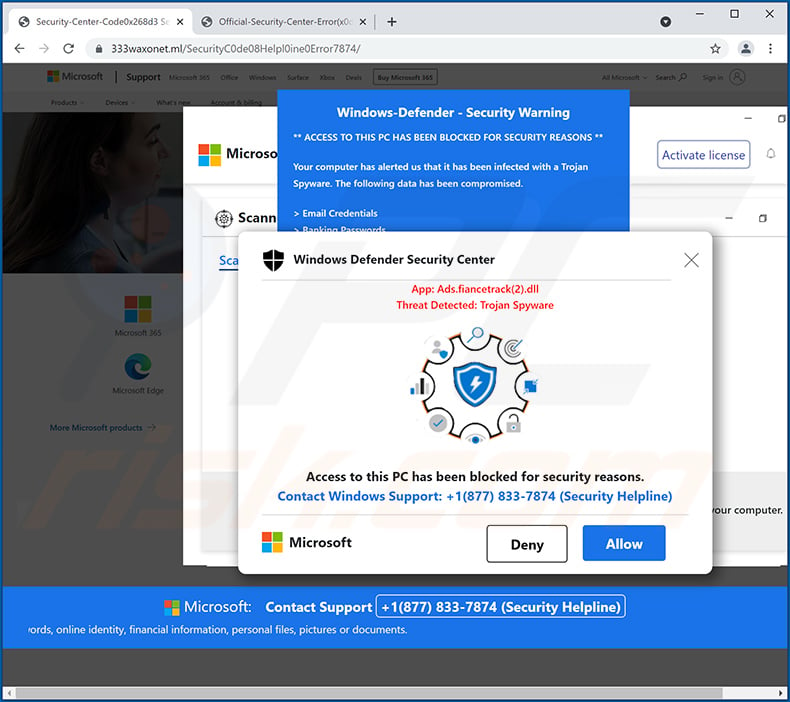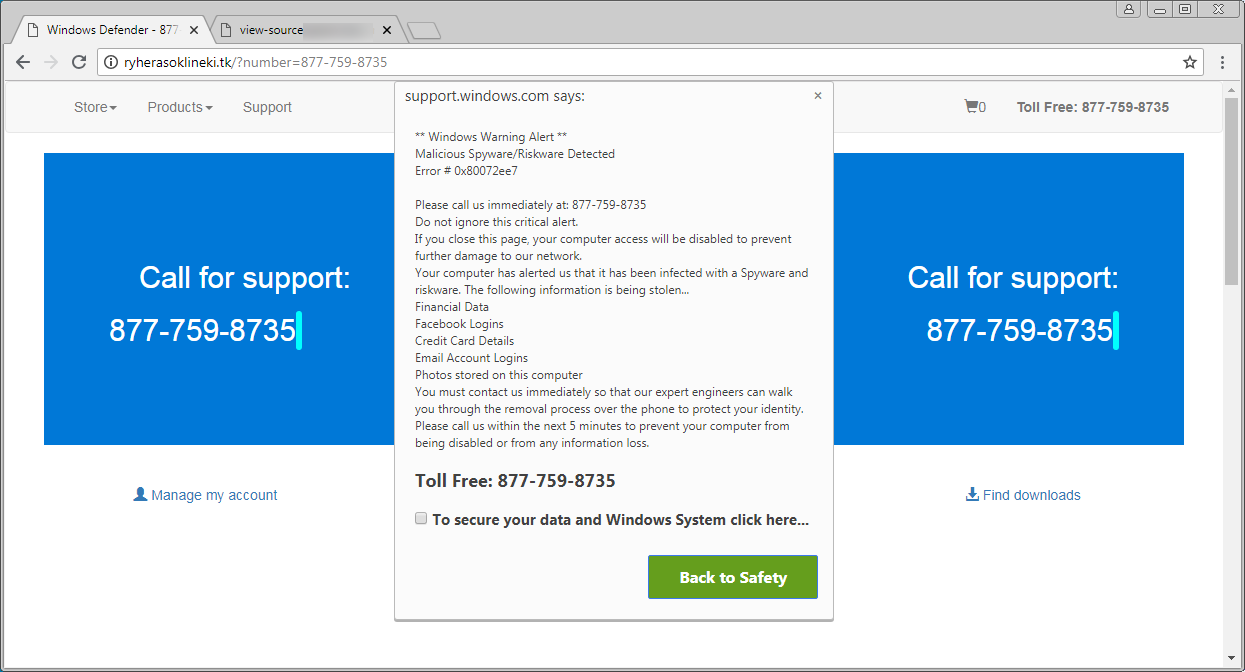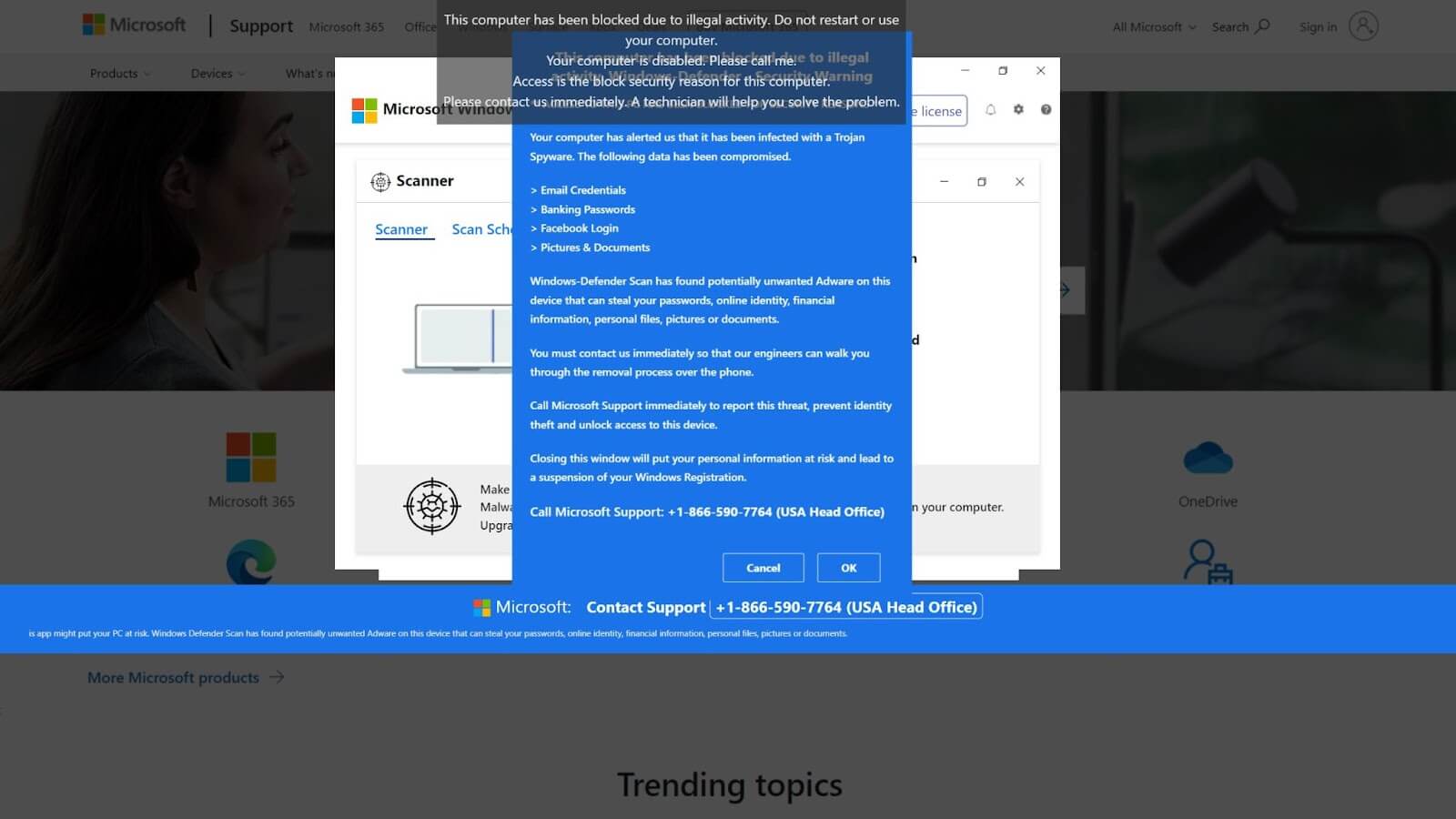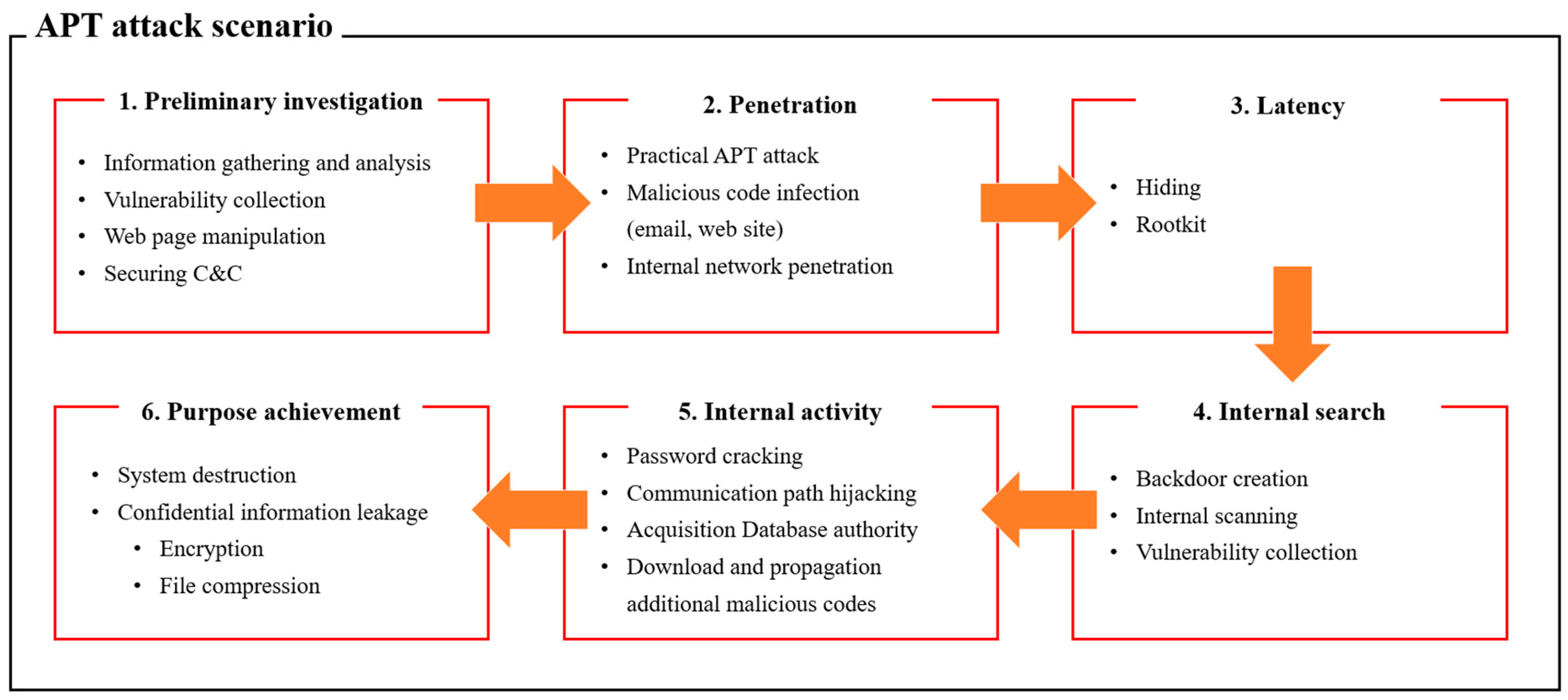
Applied Sciences | Free Full-Text | Classification and Analysis of Malicious Code Detection Techniques Based on the APT Attack

Apple Support sent me this message. Whats this mean?My phone was stolen one month ago, but I have locked my phone and turned on the Find My immediately. : r/iphone

Internet of Things security framework based on near field communication with Otway Rees protocol - Musa Jaber - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

We collected cybersecurity-related text from several OSINT sources and... | Download Scientific Diagram
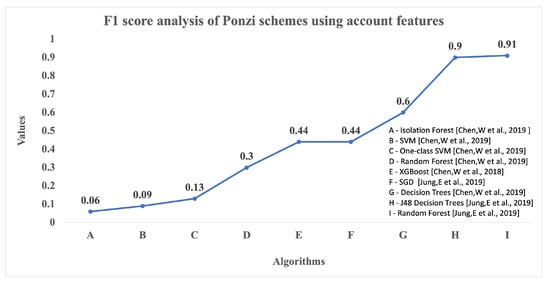
Information | Free Full-Text | Scams and Solutions in Cryptocurrencies—A Survey Analyzing Existing Machine Learning Models
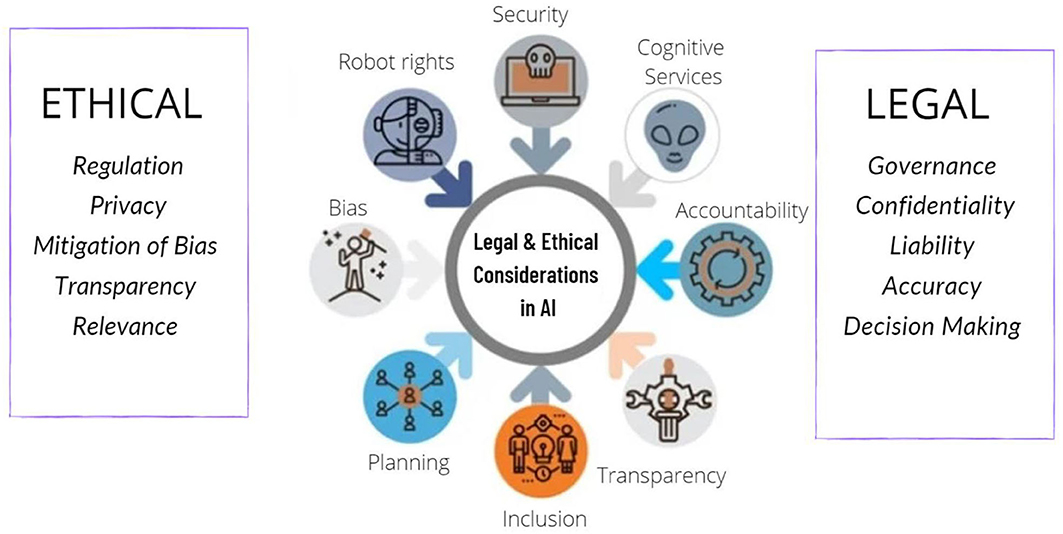
Frontiers | Legal and Ethical Consideration in Artificial Intelligence in Healthcare: Who Takes Responsibility?
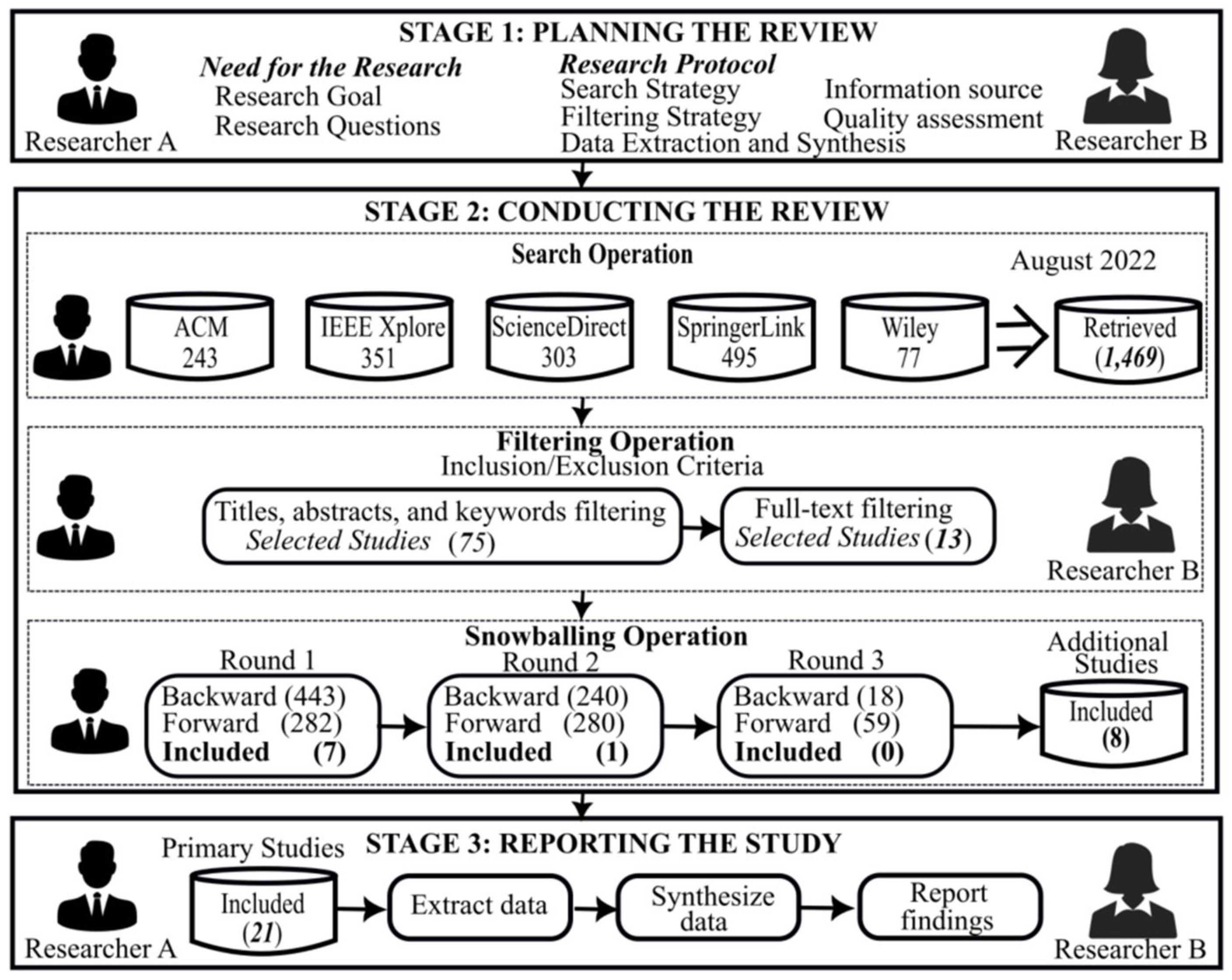
Computers | Free Full-Text | A Systematic Review on Social Robots in Public Spaces: Threat Landscape and Attack Surface